If an enterprise's digital assets are likened to a data warehouse, then DingTalk is the guardian of this warehouse. In this digital era, due to widespread use of personal phones and mobile office solutions, messages, files or screenshots sent casually by employees - due to either malicious intent or poor management - all potentially expose this database to information security risks. Data security, privacy protection and security compliance are vital to DingTalk's development. To date, DingTalk has obtained more than 15 security and compliance certifications, making it one of the enterprise office collaboration products with the most comprehensive authoritative compliance certifications. Furthermore, DingTalk Exclusive Edition, designed for medium and large customers, has exposed us to many real security incidents experienced by customers through serving numerous clients. Building upon DingTalk’s high-level security protections, we offer even more refined enterprise-specific management plans. This article will introduce how DingTalk helps businesses mitigate or resolve these security risks based on these real incidents.
If an enterprise's digital assets are likened to a data warehouse, then DingTalk is the guardian of this warehouse. In this digital era, due to widespread use of personal phones and mobile office solutions, messages, files or screenshots sent casually by employees, whether due to malicious intent or neglect in management, all potentially expose the data warehouse to information security risks.
Data security, privacy protection and security compliance are vital to DingTalk's development. To date, DingTalk has obtained more than 15 security and compliance certifications, making it one of the enterprise office collaboration products with the most comprehensive authoritative compliance certifications. Furthermore, DingTalk Exclusive Edition, designed for medium and large customers, has exposed us to many real security incidents experienced by customers through serving more clients. Based on DingTalk's high standards of security protections, we offer even more refined enterprise-specific management plans. This article will elaborate how DingTalk helps businesses prevent or resolve these security risks based on these real cases.
Identity Security
Identity Security
According to third-party reports, within the past year, 84% of surveyed enterprises experienced a data breach, of which 80% of attacks were related to identity verification, including ransomware attacks and information theft. In addition, 78% of enterprises suffered direct business losses due to identity-related breaches. DingTalk Exclusive Security manages identity verification at the account, device, and network level, implementing flexible multi-condition security checks in complex environments, addressing one of the main threats to enterprises: identity theft and unauthorized access.
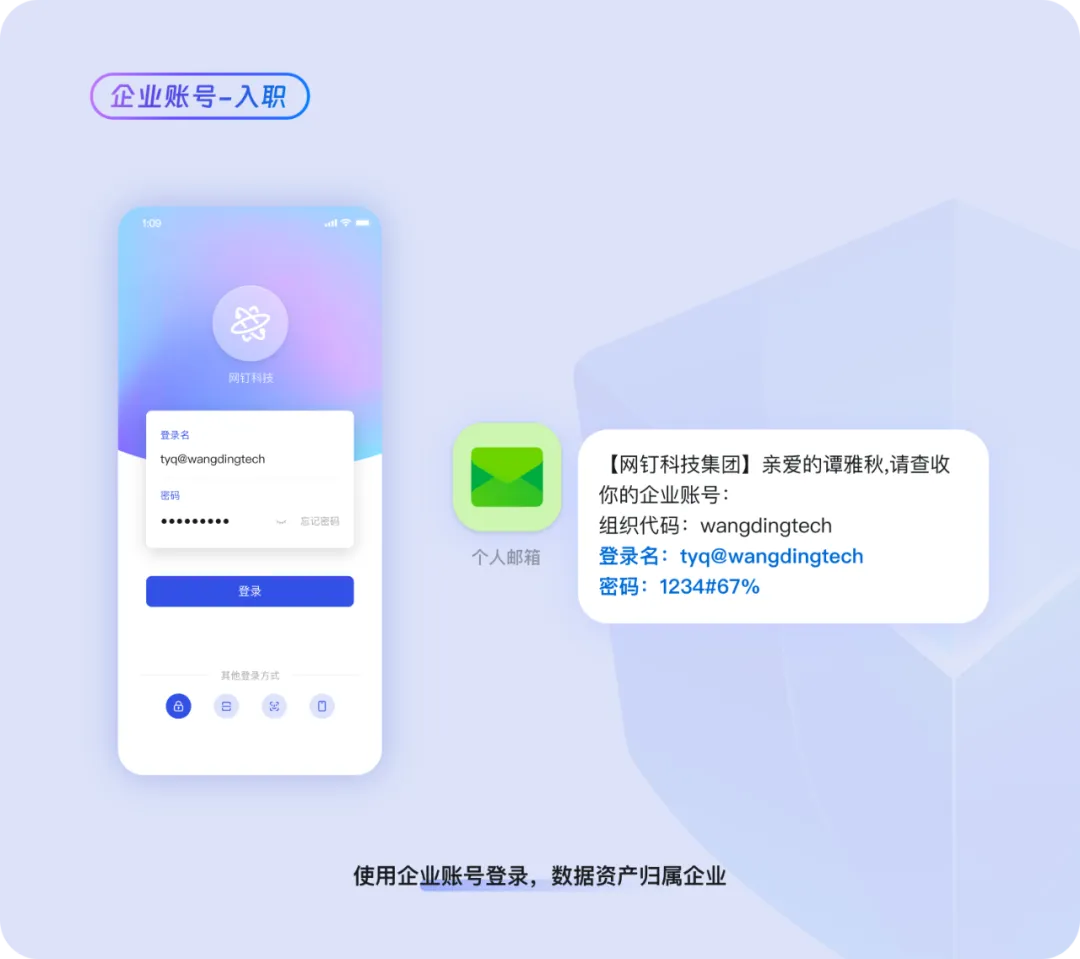
Company Accounts | Centralized Account Distribution, Data Belongs to Company
Xiaowang served as a sales person at a company. When he joined the company, he registered a personal DingTalk account and was invited by an administrator to join the company's organization. Thereafter, he used this personally registered DingTalk account for work. Two years later, Xiaowang changed jobs, bringing with him two years' worth of customer communication files, resulting in clients terminating contracts with the previous company and losses of **thousand for the company.
In order to prevent this kind of risk from happening again and enhance employee onboarding experience, the company enabled DingTalk Exclusive Edition corporate accounts. When employees log in DingTalk for the first time after joining the company, they will receive corporate account information via SMS from the company. Employees no longer need to register a DingTalk account themselves and then request to join the enterprise organization or be added by an administrator. Instead, they can directly use the company account to join. When the employee resigns, the account will be automatically deactivated and access rights will be revoked without the need for the employee to perform tedious data uploads and storage. The enterprise will not lose key data because of an individual employee's departure.
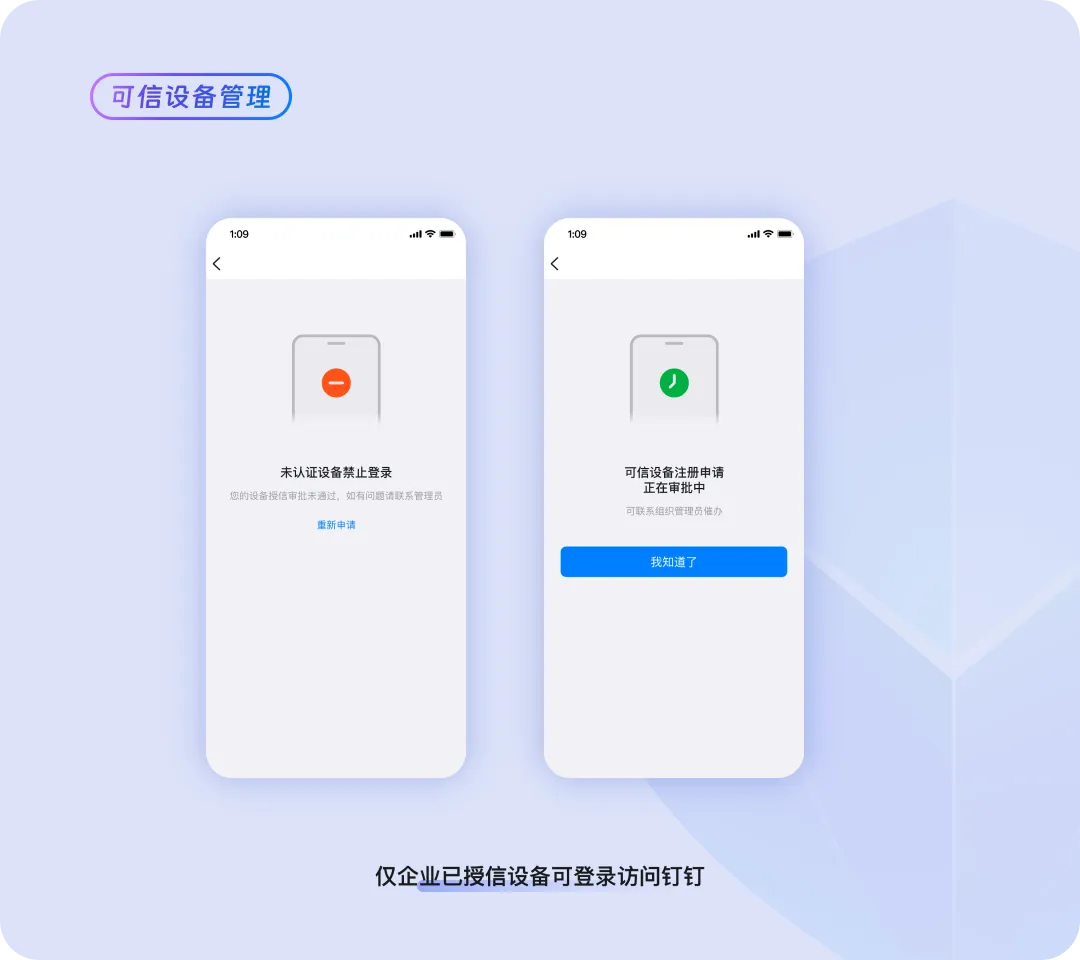
Trusted Devices | Unified Device Access Authorization Makes Mobile Office More Secure
Xiaozhang works in finance at a certain company. While traveling with his family, he accidentally lost his usual phone. The phone was logged into DingTalk and might lead to financial information leakage. Xiaozhang immediately contacted the company's administrator to report the situation and pointed out the risk of data leakage.
After being informed, the administrator removed this lost phone from the Exclusive Edition's trusted devices list in the backend system. Consequently, DingTalk on this phone was automatically logged out and prevented from re-logging in. This process quickly and easily ensured trusted access to the company data.
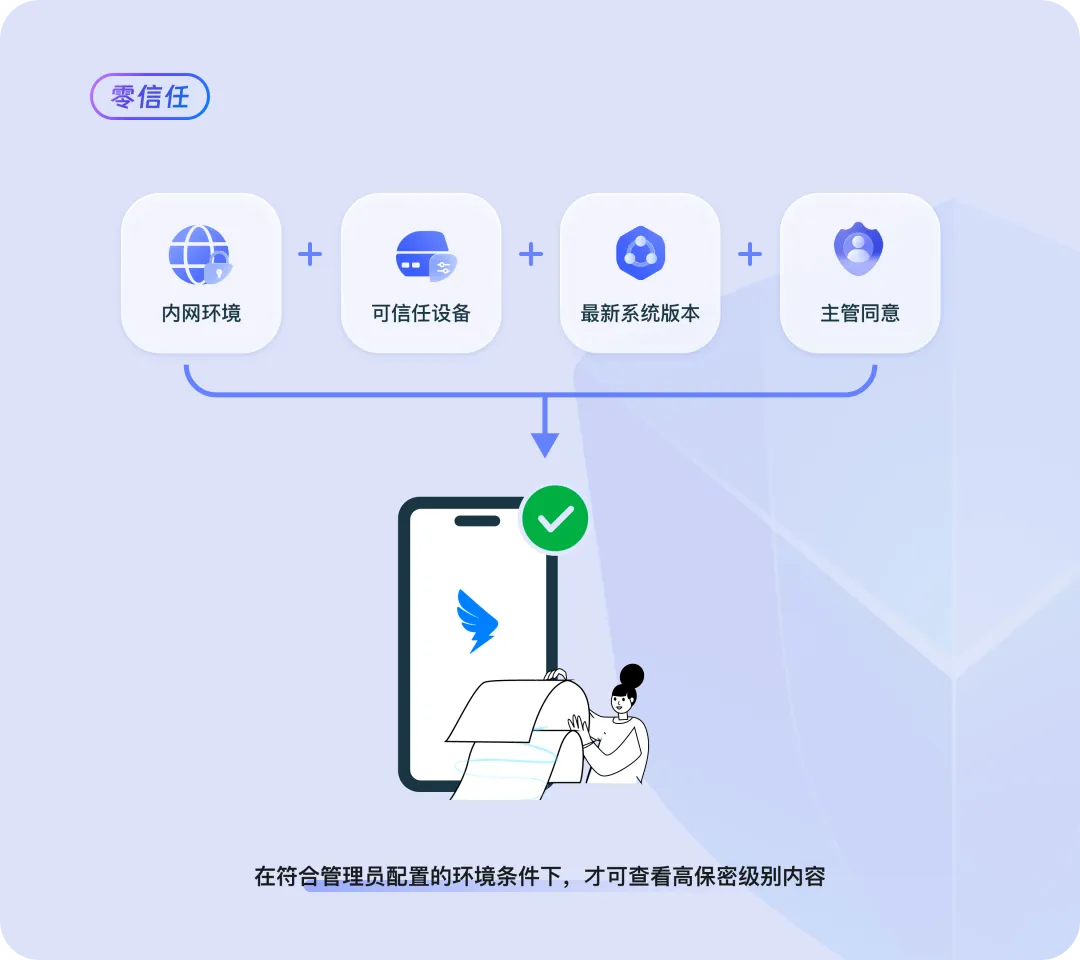
Zero Trust | A More Flexible New Security Model, Adaptable for Complex Enterprise Security Rules
Xiaoli from a company's strategic planning department needs to view the company's pre-IPO materials on DingTalk. According to company policies, this type of document contains highly sensitive data. In order to protect these sensitive data, the company stipulated: Xiaoli must be within the company's internal network, use a trusted device to log in and update the system to the latest version. Only after fulfilling all the above conditions and obtaining approval from a supervisor could he access to view the contents.
In response to such complicated data protection environments, administrators set zero-trust control rules in the background system. By decomposing complex combinations of conditions into environment factor chains connected through "and" and "or", various data protection settings can be conveniently configured. Once any unauthorized environmental change is detected after the settings, access to sensitive files is automatically prohibited.
Endpoint Security
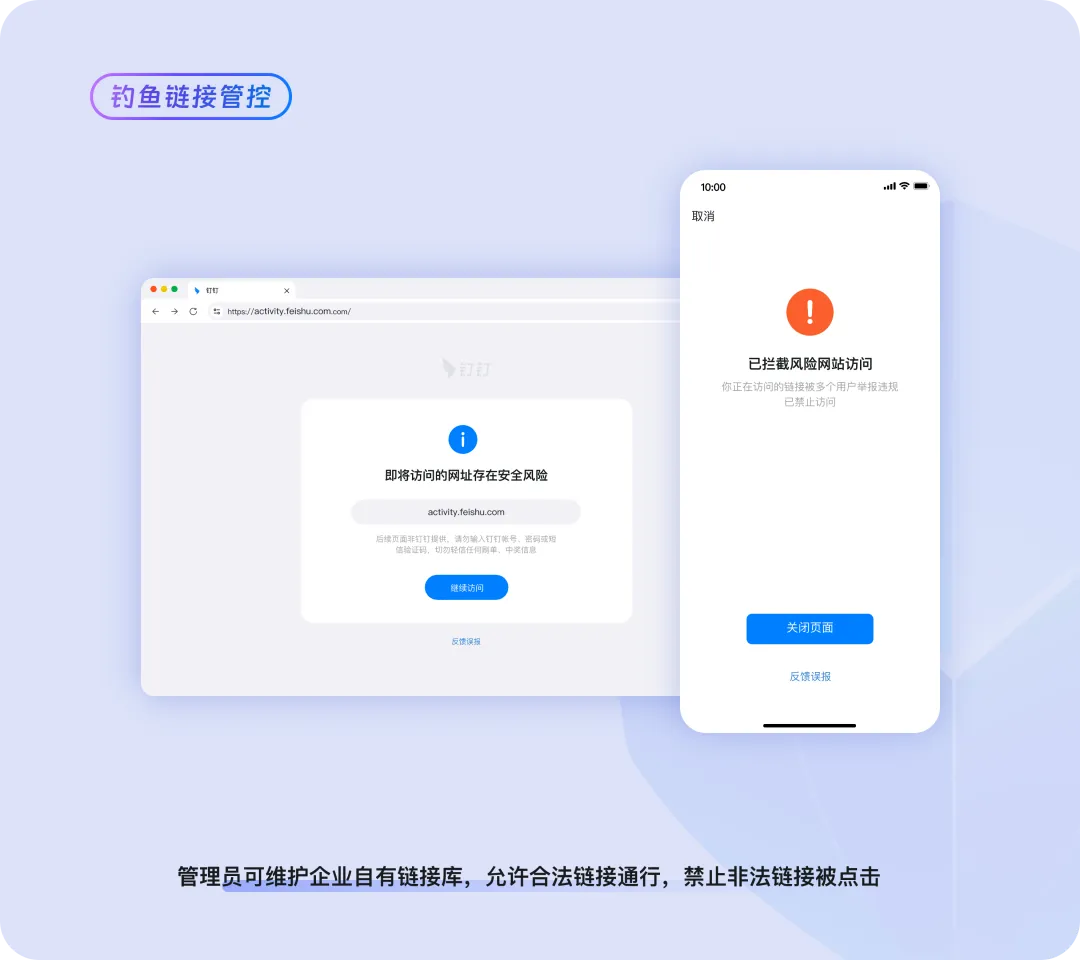
Fishing Link Management | Monitoring and Blocking Unauthorized External Links to Prevent Malicious Intrusions
An employee named Xiaohan in a company accidentally clicked an external link within a chat message. The link appeared legitimate, claiming to be an official notice about receiving subsidies, but was actually a phishing website disguised by black and grey industry actors. After clicking, Xiaohan's account was controlled, and automatically sent viruses to everyone in the company, creating a serious threat.
In order to prevent employees' mistakes from becoming another target of virus attacks, the administrator activated Exclusive Edition's fishing link management function and configured the database of risky webpage links in the backend system. In the future, if an employee accesses such a webpage, the system will prompt that this link poses data security risks and prohibits access, thereby preventing malicious intrusions and virus spreading.
Data Protection
Data Classification Level | Automatically Identify Data Classification Levels and Easily Establish a Tiered Management System
"Once files are uploaded to DingTalk, a major challenge is how our enterprise management policies for files can be implemented on DingTalk," Xiaofan, an information department officer, hopes to manage files by classification on DingTalk: implement stricter management for sensitive files, and allow free collaboration on regular files among employees, but is unsure how to identify which files are sensitive, lacking the means to establish control policies. The usual practice is that enterprise information security officers regularly train employees, distribute paper-based documents or notices about file security regulations and classification rules from high to low confidentiality level and operation procedures, reminding everyone to comply in their daily work. However, this management approach is costly and has little effect, with oversights frequently occurring.
To enhance managerial efficiency, the administrator enabled the Exclusive Edition data classification level function, automatically categorizing and tagging files after setting grading rules in the backend system, which significantly reduces training costs for employees. Simultaneously, after defining different operational rules for different classification levels, rules can be automatically implemented such as: highly confidential files cannot be forwarded to external personnel; low confidentiality files can be shared with clients as needed. This differentiated file management method prevents data leakage, improves work efficiency, and reduces management costs.
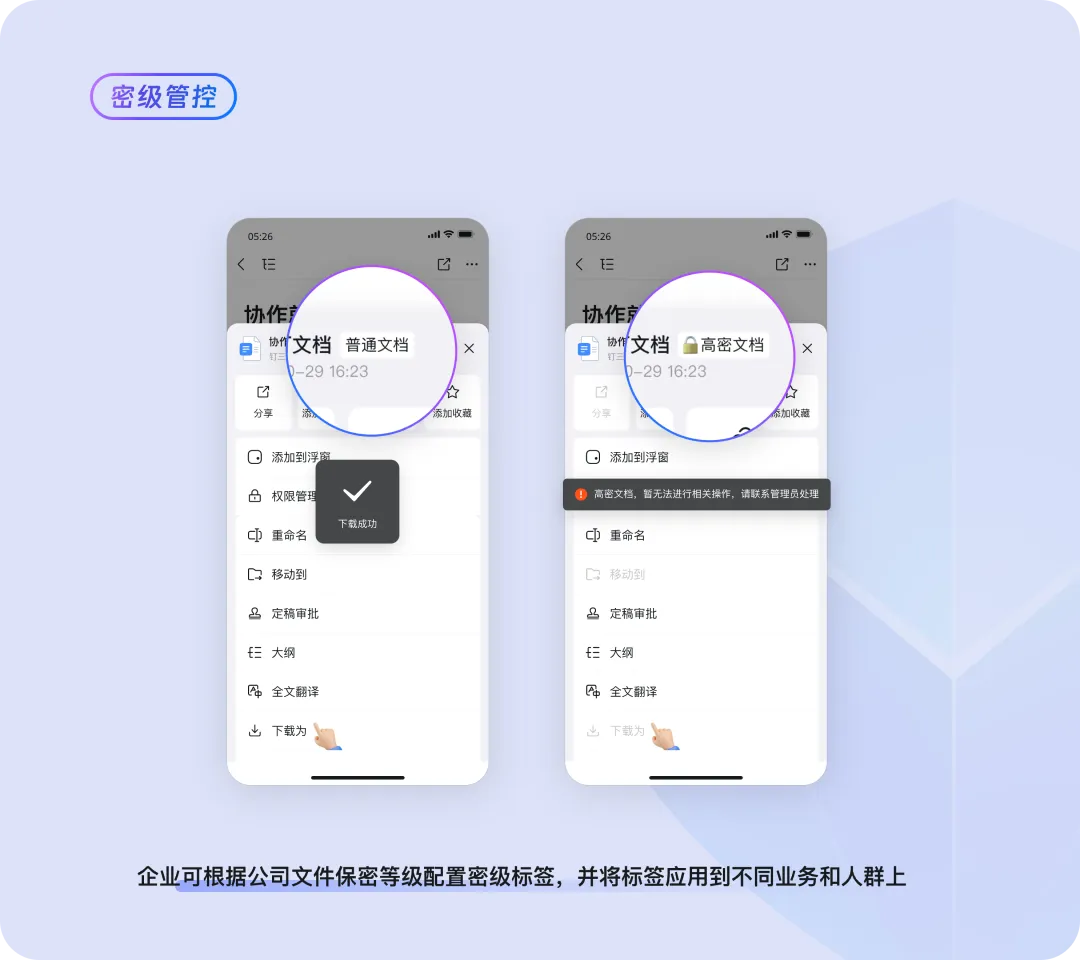
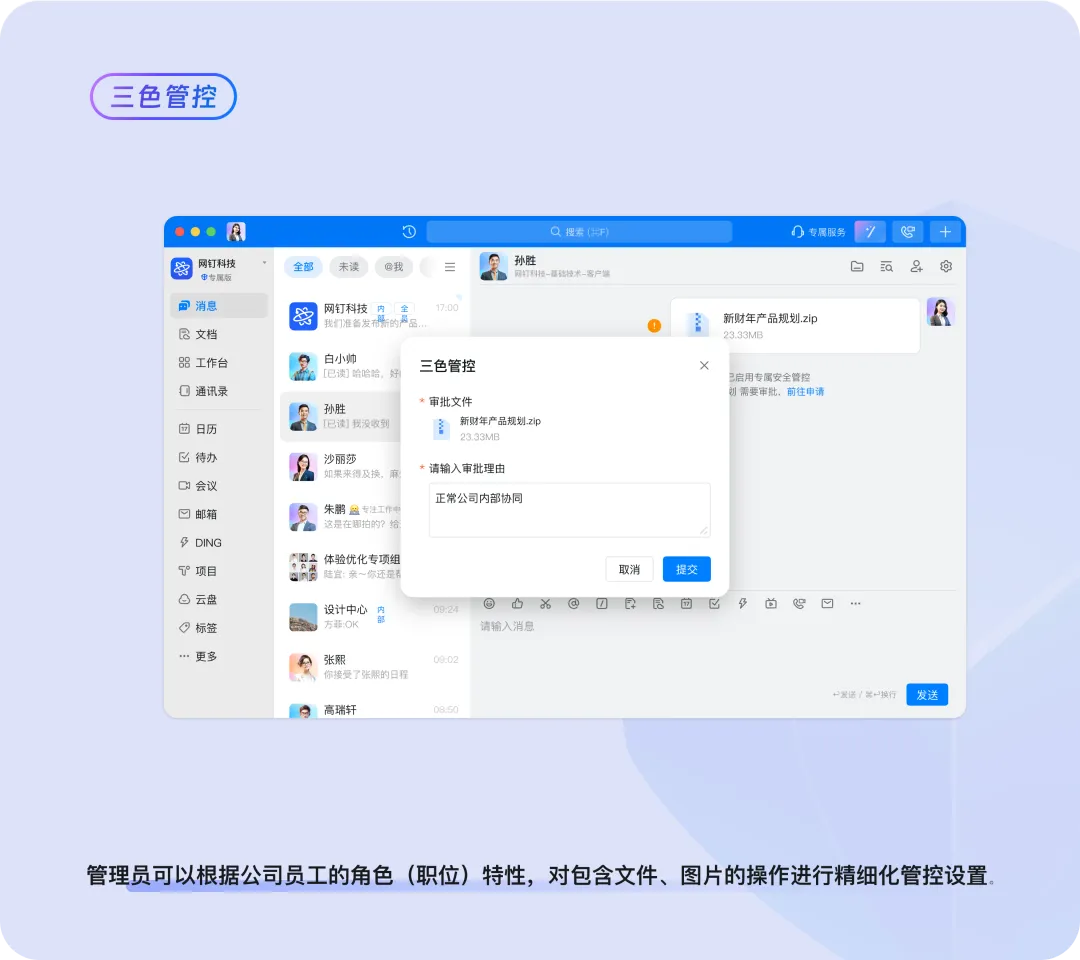
Three-level Control | Constructing a Role-based Trust System, with Permissions Dynamically Adjusted by Role
Striking a balance between security management and business collaboration efficiency has always been a difficult issue for Zhao, the head of the security department. Traditional security management was a one-size-fits-all approach—either files were forbidden from being shared between departments altogether, making collaboration inconvenient, or departments could share files freely, posing significant risks in case of an information leak.
Each enterprise consists of different departments, job positions, and internal and external collaboration scenarios. With the three-tiered control system, administrators can grant corresponding permissions to different personnel based on their role characteristics. For example, researchers who have access to core information are not allowed to send or share files externally. Functional roles, such as administrative and human resources positions, allowing them to swiftly collaborate with all internal staff by relaxing restrictions. When the control is activated, when a person in a given position attempts to send a file to a non-designated individual within another department, an automatic prompt triggers the need for approval before the file can be sent successfully. "Employees no longer complain that security management stifles business operations!"
Conclusion
DingTalk is committed to co-building a more secure enterprise office environment. Through serving numerous customers, we have accumulated extensive experience and capabilities, providing enterprises with solutions to address security threats in various real-world scenarios, comprehensively protecting enterprise digital assets.
By precisely targeting the target customer group, you can significantly improve conversion rates and marketing effectiveness. Choosing the right tools is crucial during this process. BeMail Marketing is the ideal high-efficiency, intelligent email marketing tool specially designed for modern enterprises, helping you achieve these goals more easily.
BeMail Marketing can collect leads on related platforms through keywords inputted by users according to designated collection conditions such as region, language, industry, social media and exhibitions, and obtain potential clients' email addresses. Additionally, BeMail Marketing can use AI to generate email templates, send emails to collected potential clients, track email opening status, automatically and intelligently interact with customer emails, and can also send SMS messages when necessary.
Key advantages of BeMail Marketing include:
- High delivery rate: As long as the content sent is legal and complies with regulations, and massive complaints are avoided, the delivery rate is over 90%.
- Flexible billing modes: Flexible billing by number of deliveries without time limits allows you to decide when to send emails freely.
- Global coverage capability: Utilizing global servers, it helps you smoothly deliver foreign trade promotion emails for expanding into the global market; it also supports Chinese mass email delivery, enabling easy direct access to clients' mailboxes.
- Comprehensive data analysis and optimization: Through deep analysis of user behavior and delivery data using a smart email marketing API, continuously optimize your email marketing strategy and eliminate data blind spots.
Whether you wish to gain valuable customer insights or seek a new way to improve marketing effectiveness, BeMail Marketing is a choice you can trust. For more details, please visit: https://mk.beiniuai.com
DomTech is the official DingTalk appointed service provider in Hong Kong, specializing in providing DingTalk services to a large number of customers. If you would like to learn more about the content of the DingTalk platform applications, please contact our online customer service directly. We have an excellent development and maintenance team and extensive experience in market services, capable of providing you professional DingTalk solutions and services!

 English
English
 اللغة العربية
اللغة العربية  Bahasa Indonesia
Bahasa Indonesia  日本語
日本語  Bahasa Melayu
Bahasa Melayu  ภาษาไทย
ภาษาไทย  Tiếng Việt
Tiếng Việt  简体中文
简体中文